In today’s digital world, internet connectivity has become essential for both personal and professional activities, and WiFi networks are at the heart of this connectivity. As technology has evolved, so has the security of these networks. The introduction of WiFi 6 and the WPA3 security protocol marks a significant step forward in improving the speed and security of WiFi connections. WPA3 offers robust encryption and a more secure connection compared to its predecessor, WPA2, addressing a range of vulnerabilities. Despite these advancements, many networks still rely on outdated security protocols, leaving them open to potential threats.
This article explores the progression of WiFi security, the vulnerabilities that attackers exploit, and the advancements brought by WPA3. We will also examine common WiFi attack techniques, the tools hackers use, and how WPA3 strengthens network protection.
Understanding WiFi Security: The Importance of WPA3
WiFi security has always been a critical concern, with various types of cyber-attacks targeting wireless networks. As WiFi technology continues to evolve, so do the techniques used by attackers to breach networks. WPA3, which was designed to replace the outdated WPA2 protocol, introduces several new features that offer stronger encryption and enhanced protection against common attack methods. However, while WPA3 significantly improves network security, it is not invulnerable to attacks. Understanding how WPA3 works and how it defends against common threats is crucial for anyone looking to secure their WiFi network.
Types of WiFi Attacks: How Hackers Exploit Vulnerabilities
WiFi networks are susceptible to a variety of attacks, which range in complexity. Below, we discuss the most common types of WiFi attacks that can compromise a network’s security.
1. Sniffing: The Passive Attack
Sniffing, also known as packet sniffing or eavesdropping, is a passive attack where an attacker intercepts and monitors the traffic between devices on the network. Tools like Wireshark or the Aircrack-ng suite can be used to capture data packets. Once a hacker captures the necessary information, they can attempt to decrypt passwords or gain access to sensitive data. Sniffing is particularly effective on open or poorly secured networks, such as those using WEP or WPA2 encryption.
2. Injection: Disrupting Network Traffic
WiFi networks transmit data using radio waves, which makes them susceptible to injection attacks. An attacker can send malicious packets to a targeted network, often disrupting legitimate communication or redirecting traffic. Tools like aireplay-ng or Bettercap allow attackers to perform deauthentication attacks, where devices are tricked into disconnecting and reconnecting, often under the attacker’s control. This can lead to service disruptions or data capture.
3. Cracking: Decrypting Network Passwords
WPA2 and earlier security protocols are vulnerable to cracking attacks, where an attacker tries to decipher the password of the network. By capturing a network’s handshake during the connection process, hackers can attempt to crack the password using brute force or dictionary-based methods. While WPA3 makes offline cracking much harder by requiring real-time authentication, it is still possible to crack weak WPA3 passwords using advanced techniques like brute force.
4. Rogue Access Points (Evil Twin): Deceptive Connections
An “evil twin” attack involves setting up a rogue access point that mimics a legitimate WiFi network, luring users into connecting to it. Once connected, the attacker can intercept sensitive information, including login credentials or financial data. This type of attack is particularly effective in public spaces like coffee shops or airports, where users often connect to unfamiliar networks without verifying their authenticity.
Popular WiFi Hacking Tools: Tools of the Trade
There are several powerful tools available to both attackers and security professionals for testing WiFi network security. Below are some of the most widely used tools in the WiFi hacking community.
Aircrack-ng: The Classic Tool for Network Cracking
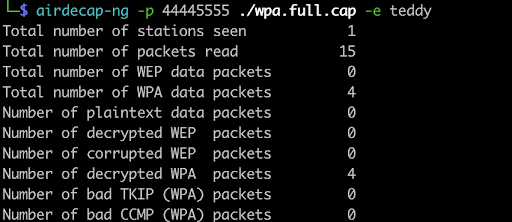
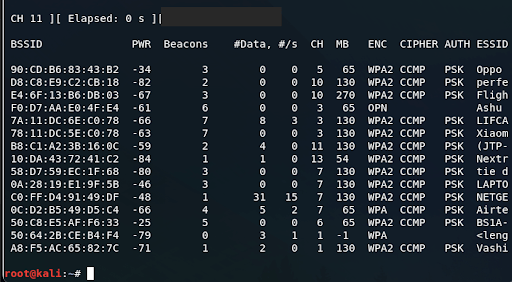
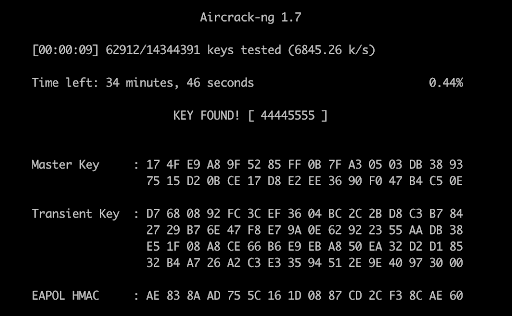
Aircrack-ng is one of the most well-known WiFi security testing tools. It includes a suite of utilities for sniffing, cracking, and injection attacks. Aircrack-ng can capture packets from wireless networks and perform offline cracking of WPA/WPA2 handshakes. It remains a staple in the WiFi hacking world due to its reliability and versatility.
Bettercap: The Versatile Network Manipulator
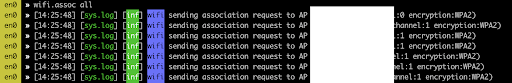

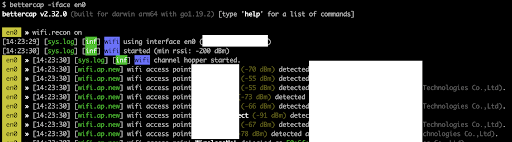
Bettercap is a newer and more comprehensive tool for performing network attacks. It supports a wide range of attacks beyond WiFi, including Bluetooth and IP-based attacks. Bettercap is particularly effective for executing deauthentication and disassociation attacks, creating rogue access points, and intercepting traffic. It also supports PMKID-based attacks on WPA2 networks, making it an essential tool for penetration testers.
WiGLE: A Global Wireless Network Database
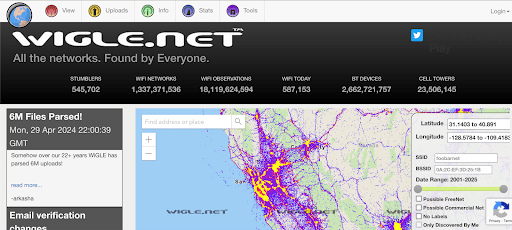
WiGLE is an online platform that allows users to map and search for wireless networks around the world. By using WiGLE, security professionals can gather intelligence on wireless networks in specific locations, aiding in penetration testing and vulnerability assessment. WiGLE is useful for discovering unprotected networks that could be targeted for attacks.
hcxtools and Hashcat: Accelerating Cracking Efforts
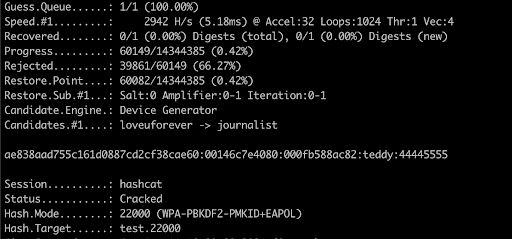
For those attempting to crack WPA2 or WPA3 passwords, hcxtools and Hashcat are indispensable tools. hcxtools can convert handshake captures into a format that Hashcat can process. Hashcat then leverages the power of modern GPUs to perform rapid password cracking, significantly reducing the time required compared to traditional CPU-based methods.
Wacker: A Tool for WPA3 Cracking Attempts

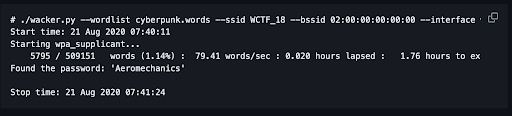
Although WPA3 offers enhanced security, tools like Wacker can still be used for attempting online brute-force attacks. While these attacks are slower and less effective than WPA2 cracking, they can still be a potential threat if a WPA3 password is weak.
How WPA3 Enhances WiFi Security: Key Features and Benefits
WPA3 was designed with modern security threats in mind, offering several important improvements over WPA2. Here are some of the key features that make WPA3 a more secure choice for WiFi networks:
Enhanced Encryption and Authentication
WPA3 utilizes more robust encryption algorithms, making it significantly harder for attackers to decrypt network traffic. The protocol also employs stronger authentication mechanisms, ensuring that devices can connect to networks securely.
Protection Against Offline Cracking
One of the major improvements of WPA3 over WPA2 is its resistance to offline cracking attacks. WPA3’s handshake process is designed to prevent hackers from capturing enough data to decrypt passwords offline. This makes brute-force cracking attempts much more difficult.
Enhanced Open Mode
WPA3 introduces an “Enhanced Open” mode for open networks, which encrypts traffic even on networks without passwords. This prevents eavesdropping on open WiFi networks, offering greater security for public or unprotected connections.
Forward Secrecy
WPA3 includes forward secrecy, meaning that even if an attacker captures past traffic, they cannot decrypt it without access to the current session’s keys. This makes WPA3 more resistant to retroactive attacks.
Frequently Asked Questions (FAQs)
1. What is the difference between WPA2 and WPA3?
WPA3 is the latest WiFi security protocol, offering stronger encryption, enhanced resistance to cracking, and better protection for open networks. Unlike WPA2, WPA3 encrypts traffic on open networks and resists offline password cracking.
2. Can WPA3 be hacked?
Although WPA3 is much more secure than WPA2, it is not immune to hacking. Weak passwords can still be cracked through online brute-force attacks, but offline cracking attempts are much more difficult and time-consuming with WPA3.
3. What tools can be used to test WiFi security?
Popular WiFi security testing tools include Aircrack-ng, Bettercap, WiGLE, hcxtools, and Hashcat. These tools help assess network vulnerabilities, crack passwords, and perform various types of attacks.
4. How can I protect my WiFi network?
To protect your WiFi network, use WPA3 encryption, choose a strong password, disable WPS (WiFi Protected Setup), and keep your router firmware up to date. It’s also important to monitor connected devices for suspicious activity.
5. Is WPA3 available on all routers?
WPA3 is supported by most modern routers, but some older devices may not be compatible. Make sure your router supports WPA3 and enable it in the settings to take full advantage of the enhanced security features.
Conclusion: Securing Your WiFi Network for the Future
As WiFi security continues to evolve, WPA3 stands as a crucial advancement in protecting wireless networks from a variety of attacks. While WPA3 offers enhanced encryption and stronger protection against common threats, it is important to stay vigilant and adopt best practices for securing your network. Upgrading to WPA3, using strong passwords, and employing security testing tools can help protect your WiFi network from malicious actors and ensure a safer digital experience. The future of WiFi security is promising, but only if we take proactive steps to stay ahead of evolving threats.

